
OWASP Juice Shop — TryHackMe
Hands-on exploits from recon to report: XSS, IDOR, SQLi, SSRF, auth bypass. Each write‑up includes steps, impact and mitigations.
Security Researcher & Penetration Tester
I do web app pentesting, bug bounty and CTF labs. Recon → exploitation → reporting.

Hands-on exploits from recon to report: XSS, IDOR, SQLi, SSRF, auth bypass. Each write‑up includes steps, impact and mitigations.
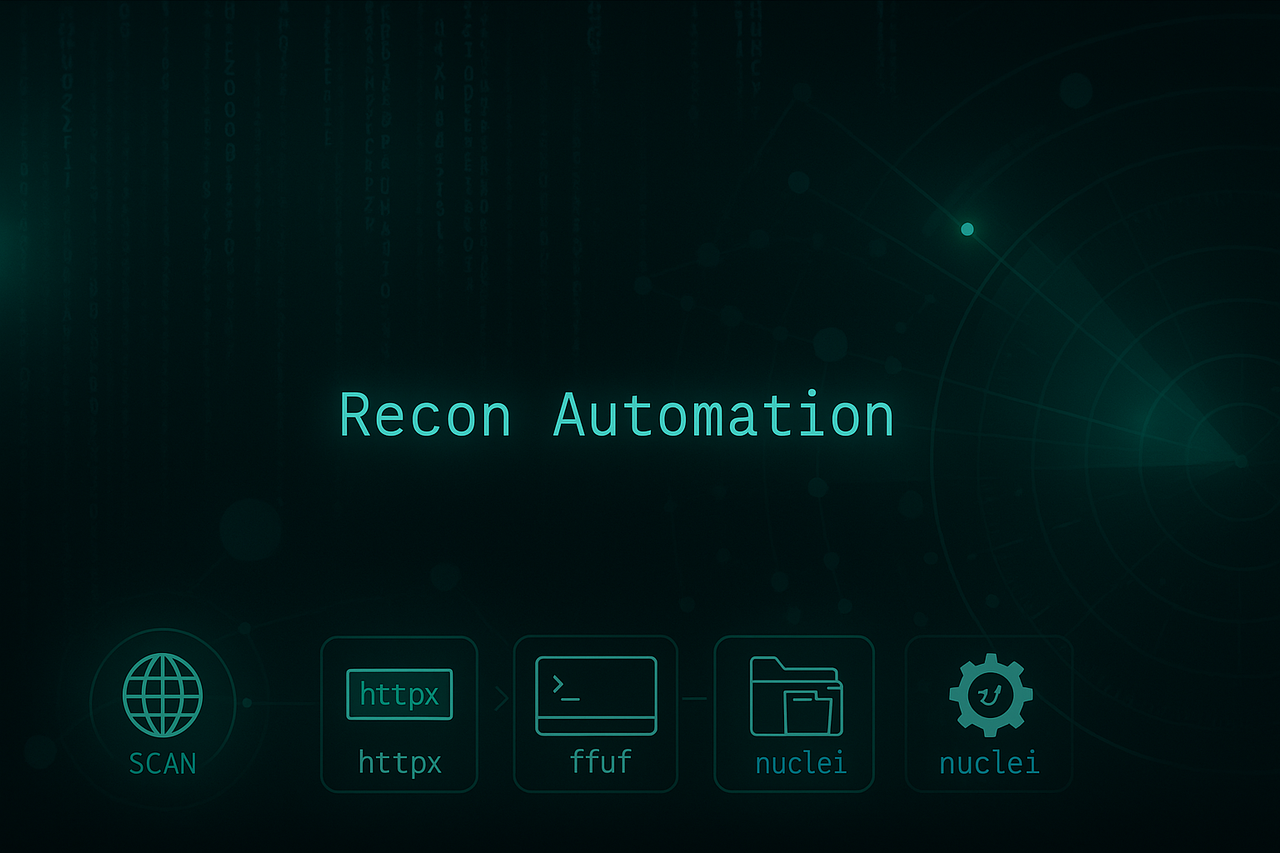
Automated subdomain discovery, alive checks, dir fuzzing, tech fingerprinting & templated nuclei scans with screenshots.
Selected challenges focusing on web exploitation, enumeration and privilege escalation. Clean notes and reproducible steps.
A few accepted/acknowledged submissions with sensitive details removed. Includes CVSS scoring and remediation guidance.
Reading ability: Comfortable reading most codebases and quickly understanding unfamiliar syntax.

I focus on web application security: crisp recon, careful testing, and remediation‑driven reports. I like turning vague bug hints into reproducible PoCs with clear business impact and fixes.
Active on Bugcrowd • HTB • THM • PortSwigger Web Security Academy.